Collective Intelligence Network Security
As our base of Sentinel IPS units has grown, we've come to realize that the attack data we gather has significant value, both to our own customers and to the community at large. Collective Intelligence Network Security (CINS, pronounced 'sins' ... get it?) is our attempt to use this information to significantly improve the security of our customers' networks and provide valuable information to the InfoSec community.
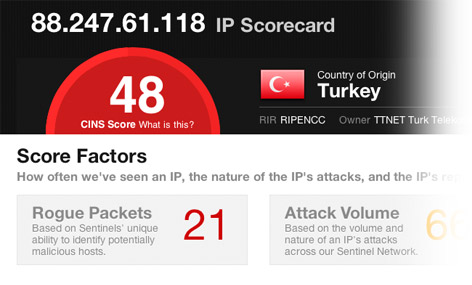
Our CINS system is constantly gathering attack data from each of our Sentinel units in the field. This data is used to calculate a CINS Score for every IP that is flagged by our system. Much like a FICO score is meant to show you at a glance the quality of your credit, the CINS Score is designed to show you the quality - the trustworthyness - of an IP address. In addition, the IP's WHOIS information, country of origin, and the nature, frequency, and breadth of its attacks across the Sentinel network are listed with the score. This level of detail is hard to replicate without an existing network like the Sentinels', and we believe this information adds tremendous value to our customers.
CINS Active Threat Intelligence
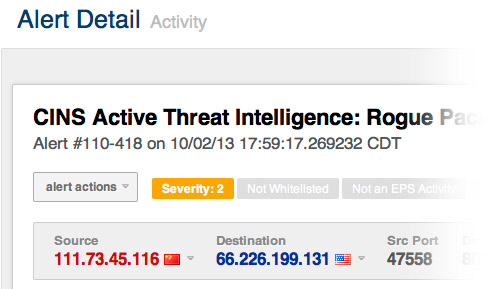
Through CINS, we can identify several classes of 'bad' IP addresses. For instance, IP addresses tend to have certain 'personalities' ... Perhaps one IP from China gains a reputation as a scanner, or maybe a certain Russian (or American) IP is prone to attacking remote desktop vulnerabilities. Of course, there are IPs all over the world that are flagged as command and control servers for malware botnets. All of these characteristics play a role in an IP's score.
We are constantly analyzing this data, and from our research we've identified certain groups of IPs - based on our specific score factors - that are malicious enough to be blocked immediately. These reputation-based rulesets generated by our CINS systems are continuously fed back out to our Sentinel network, giving each our our Sentinel customers bullet-proof protection from some of the baddest actors on the planet.
How can I access CINS Scores? Currently, CINS Scores are only available to Sentinel customers, through the Sentinel's web interface. That may change in the future as the CINS system matures, but for now we do offer the CINS Army list ...
The CINS Army List

We are joined together in our mutual belief that Internet security should be honored as a fundamental human right. We believe in your right to be connected, to be secure, and to use the Internet with freedom from malicious threats. No one should be allowed to take that away from you.
Based on these beliefs, we created the CINS Army list. CINS Army is a way for our company to give back to the community by sharing valuable threat intelligence harvested from our CINS system. The CINS Army list is a subset of the CINS Active Threat Intelligence ruleset, and consists of IP addresses that meet one of two basic criteria: 1) The IP's recent Rogue Packet score factor is very poor, or 2) The IP has tripped a designated number of 'trusted' alerts across a given number of our Sentinels deployed around the world.
The CINS Army list is here and at Emerging Threats as part of their Open Source Community. The link below is provided as a simple text file, with which you can parse and use in any way you see fit. We assume Network Administrators will use the IP addresses from this file in their firewall blacklists and possibly in custom IDS and IPS signatures.
Download the CINS Army list
Note: The CINS Army list has changed.
Please note that as of September 25th, 2017, we changed the algorithm that produces the CINS Army List, and capped the list (for now) at 15,000 IP addresses. We're excited about this change, and you can read more about it on our blog. As usual, if you have any questions or trouble with the list, please contact us at cins@sentinelips.com.
Questions?
We're hackers and coders, not copy writers. So, something not making sense? Want more information? Please don't hesitate to contact us at (972) 991-5005 or cins@sentinelips.com.
On the list?
Did your IP make it on to our CINS Active Threat Intelligence lists or the CINS Army list? False positives are very rare, but let us know and we'll work with you. Email is best: cins@sentinelips.com
Sign Up.
If this concept interests you at all, just give us an email address. Whether you want to help with the process, have any ideas, or just want to know when the CINS score database is made public in some substantial way, we'd love to hear from you. We won't sell your email address, or use it to pummel you with marketing and sales pitches (we honestly don't have time for that). We'll just keep you posted on our progress with the CINS project.


